from:http://blog.codestage.ru/2012/03/07/packed/
Packed SWF. How to unpack?
Hey, friends!
In this post I’d like to explain you what is a packed SWF, how it looks and show you some methods of dynamic and static unpacking.
So, what is packed SWF?
If you never saw it, please, feel free to download this classic example of packed SWF:
http://codestage.ru/files/flood/security/packed.swf
You can see single SWF showing a text. But you can’t reach a code showing it with a classic approach – through the decompilers.
I should mention you’ll not reach any resources (Bitmaps, Sounds, Fonts, etc) via decompilers if they will be there too, because target SWF is placed inside of SWF you have and usually it is encrypted.
Usually all you can get with decompilers from a such SWF is a decryptor/unpacker code (usually hardly obfuscated), and, probably, target encrypted SWF (if your decompiler is able to show you the DefineBinaryData tag)
This kind of packing could be achieved with simple Flex [Embed] tag.
Dynamic unpacking (dumping)
Dynamic means unpacking while target SWF is run in Flash Player (FP).
As FP can’t play packed SWF as is, it should be unpacked and decrypted into the memory before loading (as example, with Loader.loadBytes()).
More important, it will be in the memory all the time while it’s running to allow FP properly display end execute it.
That’s our chance to get it!
There are two common ways to do it.
1) Dynamic unpacking with tools
Using third-party or even own tools to automatically search SWF in FP process memory. It’s the fastest and easiest method. Doesn’t provide you a feeling you’re a true cracker ![]()
There are several tools for it available both free and paid.
One of most advanced is a SWF Revealer, free tool for the ASV licence owners. It could bypass domain checks (which will prevent SWF to unpack and decrypt) in some cases and force SWF to load and decrypt target SWF.
Also you could found some free tools for dumping after googling for it a bit.
2) Dynamic unpacking with hands
Search for it “by hands”, looking for the CWS (compressed SWF) or FWS (uncompressed SWF) header signature which are the start of any SWF file. If you never tried it, you definitely should try! It could be useful to improve your skills with hex a bit and to provide you a feeling yourself a true cracker)
For search you could use any Hex editor supporting RAM editing\viewing.
If you’ll try to search for packed SWF in the sample file I linked before, you should start from searching the FWS signature (uncompressed SWF) – just search for the ‘FWS’ string in the Flash Player’s (or Flash Player plugin\browser with SWF running in it) process because FP decompresses SWF before executing if it was compressed.
If you’ll search in a browser, be careful and close all other tabs with SWFs to decrease amount of the false positives.
Usually, you’ll find not only one signature entry, because FP contains other internal SWFs as well, like SWF showing hint how to exit from the fullscreen mode.
So if you’re not sure, I recommend you to check all found entries.
Well, what to do with found signature you’ll ask? How to validate it, how to know, where is the end of the SWF?
Please, look at this screenshot:![]()
This is a signature for the one of the SWFs found in the FP memory (accidentally it’s a signature of the target packed SWF =) ) by looking for FWS string.
So, what next? Next you should check the length of the found SWF. Length is placed at the 4 bytes starting from 4 byte:![]()
How did I knew that? It’s simple, I just read the “SWF File Format Specification” http://www.adobe.com/content/dam/Adobe/en/devnet/swf/pdf/swf_file_format_spec_v10.pdf (“The SWF header” section)
Since it’s a hexadecimal number written in memory, you should know its bytes are written from right to left. So resulting number is:
00 00 04 DB in hexadecimal and 1243 in decimal.
Let’s measure this 1243 bytes starting from the FWS signature.
Because signature starts at 053DD020, SWF file end should be at 053DD4FB (053DD020 + 4DB):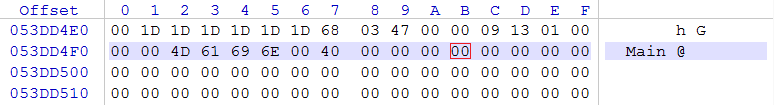
Please, note that address where FWS is placed in memory is not the same on different OS and hardware.
Now we see our SWF in memory really ends at 053DD4FB and we can select all bytes from 053DD020 up to 053DD4FB and copy-paste them into the new SWF file.
After making this with all suitable FWS entries you’ll, you’ll have target unpacked SWF file in one of the saved SWFs!
Now you should be able to decompile it as usual and look into its sources or resources.
Some protections are trying to resist SWF dumping by generating many fake FWS headers, trashing a memory with them a bit. So you should double check if header has valid length and how it looks at all. Experienced in reversing people (like me :p) could say if header fake or not just looking on it and on several tens of bytes after the header.
Sometimes, packed SWF will not be decrypted and loaded into the memory because of different cases. As example, packer’s loader could check current domain or some kind of the license file before unpacking SWF. In this case you’ll need to patch that checks (as example, with bytecode disassemblers like Yogda or RABCDasm) or provide needed files (probably with crypto keys for decrypting) to make SWF run and unpack in memory.
Static unpacking
Static means we don’t need the SWF to be executed in FP to unpack.
Well, this kind of unpacking usually comes to help when you have no chance with unpacking your SWF dynamically (who knows why you can’t run SWF?)
Static unpacking could be very difficult because of many possible safety precautions of the packer developer. There are many ways of making static unpacking painful and very long.
So, how to start with static unpacking? First of all, you should have access to the two things inside the SWF to make this unpacking possible:
1 – DefineBinaryData tag(s).
2 – Decompiled AS or abc bytecode of packer loader.
And optionally, to the
3 – SymbolClass tag
Use available tools to achieve it (ASV, Adobe SWF Investigator, SWiX, etc).
How to find DefineBinaryData tag in the SWF?
Well, some tools, like ASV will point you to that tag with ease and allow you to save it as binary file.
Also it could be found by hands, with different tag-reading tools, like mentioned before Adobe SWF Investigator.
To get data from DefineBinaryData tag with Adobe SWF Investigator from the sample file I linked above, just open the file, go to the Tag Viewer tab, select DefineBinaryData tag and press Dump To File button.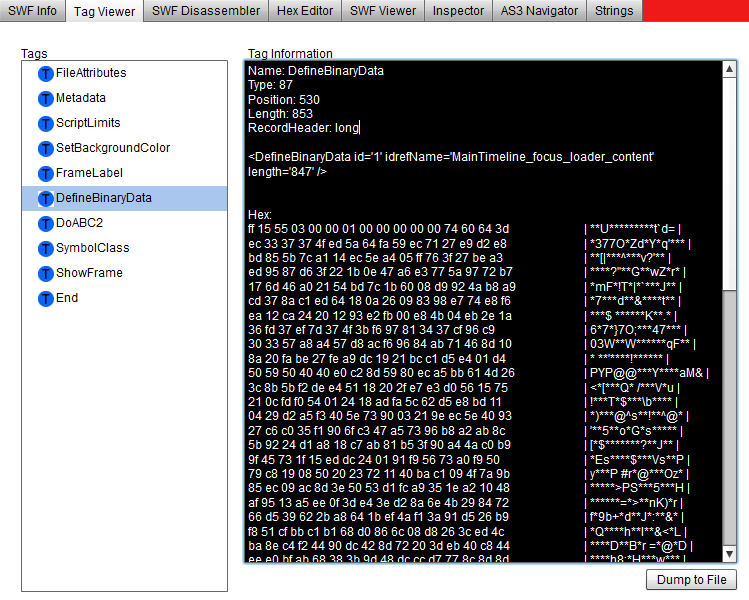
Sometimes there could be numerous fake DefineBinaryData tags inside, just to make your life harder. To find the desired tag, you should look inside the packer’s loader code and track down where is the embedded SWF is created to be decrypted and loaded.
Usually it looks like this:
var someVar:ByteArray = new SomeClass();
Where SomeClass is type of Class extending the ByteArrayAsset class.
Let’s look at the sample SWF loader code and look for something like this.
Gotcha! here it is:
private var content:Class; //... var _local3:ByteArray = new this.content();
So, we should look for the class with name ending on “_content” and extending the ByteArrayAsset class.
We have one match here:
public class MainTimeline_focus_loader_content extends ByteArrayAsset
To get which DefineBinaryData tag is linked with this class, we should look into the SymbolClass tag and search there for a record with found class name “MainTimeline_focus_loader_content”.
And we got it (in Adobe SWF Investigator):
<Symbol idref='1' className='MainTimeline_focus_loader_content' />
Remember idref value. This is a desired DefineBinaryData tag id!
Now go and search the DefineBinaryData tag with id = 1 – that tag will be needed one, so we can just dump it in a file and continue unpacking.
Why I asked you to remember the idref value instead of class name? That’s because in case loader AS will be obfuscated, it could be really hard to work with class name.
Now your success depends on your free time, packer’s loader difficulty and your luck)
If you’ll be a lucky one, that data dumped from the DefineBinaryData tag will be the pure, not encrypted SWF, and unpacking will be finished.
But in most cases data is encrypted and you should reverse engineer the packer’s loader code and make own decryptor.
In our case the loader’s code is extremely easy and not obfuscated, so we can easily found the decryption function:
private function decryptFile(_arg1:ByteArray):void
{
_arg1.position = 0;
var _local2:int = -1;
var _local3:uint = _arg1.length;
var _local4:uint = uint("55");
while (_local2++ < _local3)
{
_arg1[_local2] = (_arg1[_local2] ^ _local4);
};
}
All we need to decrypt file from the DefineBinaryData tag is just xor each byte of it by 55.
That’s all. Now you could write decryptor, decrypt SWF and decompile it to see the desired source code. And pray this decrypted swf will be your target swf, not the another one with packed swf inside haha! Sometimes packers uses the Russian Matreshka doll approach to hide target swf and other techniques to make static unpacking harder. Anyway, dynamic unpacking will beat all of them.
Remember – in Flash world, nothing only variables names can be hided from the true professional with high motivation level.
Any questions, ideas, comments? Feel free to leave it below!






相关推荐
About This Book Explore various tools and their strengths while building meaningful representations that can make it easier to understand data Packed with computational methods and algorithms in ...
MF_0000_packed.raw
It's the fastest-growing, coolest Linux distribution out there, and now you can join the excitement with this information-packed guide. Want to edit graphics? Create a spreadsheet? Manage groups? Set ...
Terrain To Mesh 2021 is new rebuild, upgraded and improved version of Terrain To Mesh which is on the market since 2015. Owners of the old (now deprecated) Terrain To Mesh can use price reduced ...
Packed with plenty of code samples, you will understand how to define the repositories that contain dependencies. Following this, you will learn how to customize the dependency resolution process in ...
packed.(我包里装了……。)等。 在对话部分,学生可以通过听力和阅读来理解和master新词汇和句式。例如,在对话1中,学生需要理解"I just called the travel agency. It’s all set. On July first, I’m ...
* 疑问形式:Have/Has...got...? 5. Have you got enough space in your suitcase?:行箱的空间够大吗? * enough + n.:足够的,足够的数量 本文档对牛津英语上海版六年级下册的知识点进行了详细的整理和解释,...
永大解密软件修改版本V2.0_packed.exe
This is a program to dump .NET packed applications. Of course no serious .NET protection relies on packing. In fact, this software shows how easily you can unpack a protected assemly. This .NET ...
And as a team, you’ll gain a vocabulary and a means to coordinate how to write and organize automated tests for the web. Follow the testing pyramid and level up your skills in user interface testing...
【FMQA-packed测试记录表详解】 在IT行业中,质量管理是至关重要的环节,特别是在产品开发与生产过程中。"FMQA-packed test record.doc" 提到的文件是一种用于管理质量保证的工具,它专注于产品包装阶段的质量控制...
替换新的文件,无限转换,替换新的文件,
"mz-packed图片放大镜"是一款基于JavaScript技术实现的图片查看工具,专为网页环境设计,提供便捷的图片放大查看功能。它具有轻量级、无水印的特点,使得用户在网页上可以清晰地查看细节丰富的图片,而不会受到任何...
Mesh Materializer is a collection of tools that help you move project to a new level of visual style. Tutorial videos Package includes: 1) Low Poly Mesh Generator. 2) Ambient Occlusion and ...
42. all you have to do:你只需要做...,强调简单易行。 43. always the case:常常如此,表示情况一贯如此。 44. ambulance chaser:唯利是图的律师,专接事故赔偿案件。 45. apple-polish:讨好,奉承别人。 46. ...
【标题】"cri packed file maker" 是一个专用于处理CPK格式文件的工具,它简化了解包过程,使得用户能够快速、便捷地对CPK文件进行操作。CPK(Compressed Package)是一种常见的数据打包格式,尤其在游戏行业中广泛...
将您要提取的所有文件放在packed文件夹中,然后运行适当的文件进行解packed 。 unpack.bat , unpack.command或unpack.sh 。 打包XNB文件 将您希望重新打包的所有文件放回unpacked文件夹中的XNB文件中,并运行适当...