ACID: Database (v100-103) ER Diagram
Snort (and other devices) log to database with the following schema:
Snort 1.8 (DB v100-103) and ACID 0.9.6b10 Database ER diagram
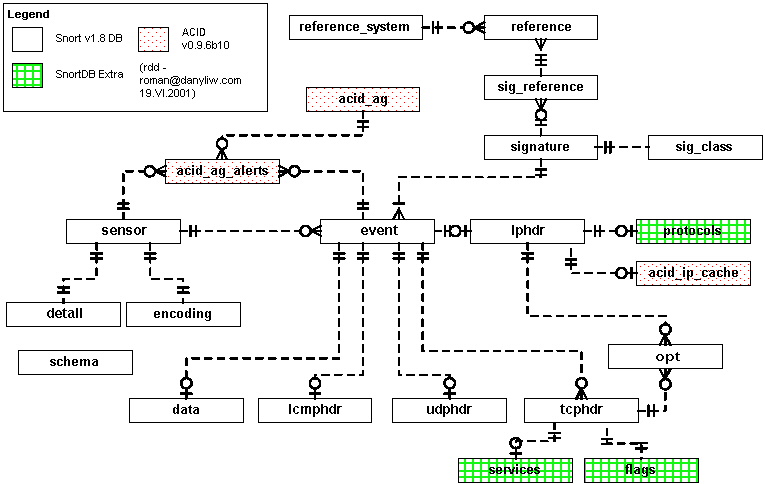
| Table | Component | Description |
| schema | Snort | Self-documented information about the database |
| sensor | Snort | Sensor name |
| event | Snort | Meta-data about the detected alert |
| signature | Snort | Normalized listing of alert/signature names, priorities, and revision IDs |
| sig_reference | Snort | Reference information for a signature |
| reference | Snort | Reference IDs for a signature |
| reference_system | Snort | (lookup table) Reference system list |
| sig_class | Snort | Normalized listing of alert/signature classifications |
| data | Snort | Contents of packet payload |
| iphdr | Snort | IP protocol fields |
| tcphdr | Snort | TCP protocol fields |
| udphdr | Snort | UDP protocol fields |
| icmphdr | Snort | ICMP protocol fields |
| opt | Snort | IP and TCP options |
detail |
Snort | (lookup table) Level of detail with which a sensor is logging |
encoding |
Snort | (lookup table) Type of encoding used for the packet payload |
protocols |
SnortDB extra | (lookup table) Layer-4 (IP encoded) protocol list |
services |
SnortDB extra | (lookup table) TCP and UDP service list |
flags |
SnortDB extra | (lookup table) TCP flag list |
| acid_ag | ACID | Meta-data for alert groups |
| acid_ag_alert | ACID | Alerts in each alert group |
| acid_ip_cache | ACID | Cached DNS and whois information |
schema
+-------+------------------+------+-----+---------------------+----------------------------------------+ | Field | Type | Null | Key | Default | Description | +-------+------------------+------+-----+---------------------+----------------------------------------+ | vseq | int(10) unsigned | | PRI | 0 | Database schema ID number (e.g. '102') | | ctime | datetime | | | 0000-00-00 00:00:00 | Timestamp of database creation time | +-------+------------------+------+-----+---------------------+----------------------------------------+
sensor
+-----------+------------------+------+-----+---------+----------------------------------------------+ | Field | Type | Null | Key | Default | Description | +-----------+------------------+------+-----+---------+----------------------------------------------+ | sid | int(10) unsigned | | PRI | NULL | Sensor ID | | hostname | text | YES | | NULL | Hostname of the sensor (IP if can't qualify) | | interface | text | YES | | NULL | Network interface (e.g. eth0) | | filter | text | YES | | NULL | BPF filter | | detail | tinyint(4) | YES | | NULL | Detail level of the logging | | encoding | tinyint(4) | YES | | NULL | Encoding format of the payload | +-----------+------------------+------+-----+---------+----------------------------------------------+
event
+-----------+------------------+------+-----+---------------------+----------------------------------------+ | Field | Type | Null | Key | Default | Description | +-----------+------------------+------+-----+---------------------+----------------------------------------+ | sid | int(10) unsigned | | PRI | 0 | Sensor ID | | cid | int(10) unsigned | | PRI | 0 | Event ID | | signature | int(10) unsigned | | MUL | 0 | Signature ID | | timestamp | datetime | | MUL | 0000-00-00 00:00:00 | Timestamp of when the event was logged | +-----------+------------------+------+-----+---------------------+----------------------------------------+
signature
+--------------+------------------+------+-----+---------+-----------------------+ | Field | Type | Null | Key | Default | Description | +--------------+------------------+------+-----+---------+-----------------------+ | sig_id | int(10) unsigned | | PRI | NULL | Signature ID | | sig_name | varchar(255) | | MUL | | Signature Name | | sig_class_id | int(10) unsigned | YES | MUL | NULL | Classification ID | | sig_priority | int(10) unsigned | YES | | NULL | Priority | | sig_rev | int(10) unsigned | YES | | NULL | Revision number | | sig_sid | int(10) unsigned | YES | | NULL | Internal signature ID | +--------------+------------------+------+-----+---------+-----------------------+
sig_reference
+---------+------------------+------+-----+---------+-------------------------------------------------+ | Field | Type | Null | Key | Default | Description | +---------+------------------+------+-----+---------+-------------------------------------------------+ | sig_id | int(10) unsigned | | PRI | 0 | Signature ID | | ref_seq | int(10) unsigned | | PRI | 0 | Reference sequence number (multiple references) | | ref_id | int(10) unsigned | | | 0 | Reference ID | +---------+------------------+------+-----+---------+-------------------------------------------------+
reference
+---------------+------------------+------+-----+---------+--------------------------------------+ | Field | Type | Null | Key | Default | Description | +---------------+------------------+------+-----+---------+--------------------------------------+ | ref_id | int(10) unsigned | | PRI | NULL | Reference ID | | ref_system_id | int(10) unsigned | | | 0 | Reference system ID | | ref_tag | varchar(20) | | | | Reference tag (e.g. CVE-CAN-2001-01) | +---------------+------------------+------+-----+---------+--------------------------------------+
reference_system
+-----------------+------------------+------+-----+---------+----------------------------------+ | Field | Type | Null | Key | Default | Description | +-----------------+------------------+------+-----+---------+----------------------------------+ | ref_system_id | int(10) unsigned | | PRI | NULL | Reference system ID | | ref_system_name | varchar(20) | YES | | NULL | Reference system name (e.g. CVE) | +-----------------+------------------+------+-----+---------+----------------------------------+
sig_class
+----------------+------------------+------+-----+---------+----------------------------------+ | Field | Type | Null | Key | Default | Description | +----------------+------------------+------+-----+---------+----------------------------------+ | sig_class_id | int(10) unsigned | | PRI | NULL | Signature classification ID | | sig_class_name | varchar(60) | | MUL | | Classification name (e.g. recon) | +----------------+------------------+------+-----+---------+----------------------------------+
data
+--------------+------------------+------+-----+---------+-----------------------------------------------------+ | Field | Type | Null | Key | Default | Description | +--------------+------------------+------+-----+---------+-----------------------------------------------------+ | sid | int(10) unsigned | | PRI | 0 | Sensor ID | | cid | int(10) unsigned | | PRI | 0 | Event ID | | data_payload | text | YES | | NULL | Packet payload encoded according to sensor.encoding | +--------------+------------------+------+-----+---------+-----------------------------------------------------+
iphdr
+----------+----------------------+------+-----+---------+----------------------------------------------+ | Field | Type | Null | Key | Default | Description | +----------+----------------------+------+-----+---------+----------------------------------------------+ | sid | int(10) unsigned | | PRI | 0 | Sensor ID | | cid | int(10) unsigned | | PRI | 0 | Event ID | | ip_src | int(10) unsigned | | MUL | 0 | Source IP address (32-bit unsigned int) | | ip_dst | int(10) unsigned | | MUL | 0 | Destination IP address (32-bit unsigned int) | | ip_ver | tinyint(3) unsigned | YES | | NULL | IP version | | ip_hlen | tinyint(3) unsigned | YES | | NULL | IP Header length | | ip_tos | tinyint(3) unsigned | YES | | NULL | IP type-of-service | | ip_len | smallint(5) unsigned | YES | | NULL | IP datagram length | | ip_id | smallint(5) unsigned | YES | | NULL | IP ID | | ip_flags | tinyint(3) unsigned | YES | | NULL | IP flags | | ip_off | smallint(5) unsigned | YES | | NULL | IP fragment offset | | ip_ttl | tinyint(3) unsigned | YES | | NULL | IP time-to-live | | ip_proto | tinyint(3) unsigned | | | 0 | IP protocol | | ip_csum | smallint(5) unsigned | YES | | NULL | IP checksum | +----------+----------------------+------+-----+---------+----------------------------------------------+
tcphdr
+-----------+----------------------+------+-----+---------+----------------------+ | Field | Type | Null | Key | Default | Description | +-----------+----------------------+------+-----+---------+----------------------+ | sid | int(10) unsigned | | PRI | 0 | Sensor ID | | cid | int(10) unsigned | | PRI | 0 | Event ID | | tcp_sport | smallint(5) unsigned | | MUL | 0 | TCP source port | | tcp_dport | smallint(5) unsigned | | MUL | 0 | TCP destination port | | tcp_seq | int(10) unsigned | YES | | NULL | TCP sequence number | | tcp_ack | int(10) unsigned | YES | | NULL | TCP ACK number | | tcp_off | tinyint(3) unsigned | YES | | NULL | TCP offset | | tcp_res | tinyint(3) unsigned | YES | | NULL | TCP reserved | | tcp_flags | tinyint(3) unsigned | | MUL | 0 | TCP flags | | tcp_win | smallint(5) unsigned | YES | | NULL | TCP window | | tcp_csum | smallint(5) unsigned | YES | | NULL | TCP checksum | | tcp_urp | smallint(5) unsigned | YES | | NULL | TCP urgent pointer | +-----------+----------------------+------+-----+---------+----------------------+
udphdr
+-----------+----------------------+------+-----+---------+----------------------+ | Field | Type | Null | Key | Default | Description | +-----------+----------------------+------+-----+---------+----------------------+ | sid | int(10) unsigned | | PRI | 0 | Sensor ID | | cid | int(10) unsigned | | PRI | 0 | Event ID | | udp_sport | smallint(5) unsigned | | MUL | 0 | UDP soure port | | udp_dport | smallint(5) unsigned | | MUL | 0 | UDP destination port | | udp_len | smallint(5) unsigned | YES | | NULL | UDP length | | udp_csum | smallint(5) unsigned | YES | | NULL | UDP checksum | +-----------+----------------------+------+-----+---------+----------------------+
icmphdr
+-----------+----------------------+------+-----+---------+----------------------+ | Field | Type | Null | Key | Default | Description | +-----------+----------------------+------+-----+---------+----------------------+ | sid | int(10) unsigned | | PRI | 0 | Sensor ID | | cid | int(10) unsigned | | PRI | 0 | Event ID | | icmp_type | tinyint(3) unsigned | | MUL | 0 | ICMP type | | icmp_code | tinyint(3) unsigned | | | 0 | ICMP code | | icmp_csum | smallint(5) unsigned | YES | | NULL | ICMP checksum | | icmp_id | smallint(5) unsigned | YES | | NULL | ICMP ID | | icmp_seq | smallint(5) unsigned | YES | | NULL | ICMP sequence number | +-----------+----------------------+------+-----+---------+----------------------+
opt
+-----------+---------------------+------+-----+---------+----------------------------------------+ | Field | Type | Null | Key | Default | Description | +-----------+---------------------+------+-----+---------+----------------------------------------+ | sid | int(10) unsigned | | PRI | 0 | Sensor ID | | cid | int(10) unsigned | | PRI | 0 | Event ID | | optid | int(10) unsigned | | PRI | 0 | Option ID (multiple options per alert) | | opt_proto | tinyint(3) unsigned | | | 0 | Option protocol (IP, TCP) | | opt_code | tinyint(3) unsigned | | | 0 | Option code | | opt_len | smallint(6) | YES | | NULL | Option length | | opt_data | text | YES | | NULL | Option data | +-----------+---------------------+------+-----+---------+----------------------------------------+
acid_ag
+----------+------------------+------+-----+---------+-----------------------------------+ | Field | Type | Null | Key | Default | Description | +----------+------------------+------+-----+---------+-----------------------------------+ | ag_id | int(10) unsigned | | PRI | NULL | Alert Group (AG) ID | | ag_name | varchar(40) | YES | | NULL | AG name | | ag_desc | text | YES | | NULL | AG description | | ag_ctime | datetime | YES | | NULL | Timestamp of AG creation time | | ag_ltime | datetime | YES | | NULL | Timestamp of last AG modification | +----------+------------------+------+-----+---------+-----------------------------------+
acid_ag_alert
+--------+------------------+------+-----+---------+---------------------+ | Field | Type | Null | Key | Default | Description | +--------+------------------+------+-----+---------+---------------------+ | ag_id | int(10) unsigned | | PRI | 0 | Alert Group (AG) ID | | ag_sid | int(10) unsigned | | PRI | 0 | Sensor ID | | ag_cid | int(10) unsigned | | PRI | 0 | Event ID | +--------+------------------+------+-----+---------+---------------------+
acid_ip_cache
+---------------------+------------------+------+-----+---------+----------------------------------+ | Field | Type | Null | Key | Default | Description | +---------------------+------------------+------+-----+---------+----------------------------------+ | ipc_ip | int(10) unsigned | | PRI | 0 | IP address (32-bit unsigned int) | | ipc_fqdn | varchar(50) | YES | MUL | NULL | FQDN | | ipc_dns_timestamp | datetime | YES | | NULL | DNS lookup timestamp | | ipc_whois | text | YES | | NULL | whois information | | ipc_whois_timestamp | datetime | YES | | NULL | whois lookup time | +---------------------+------------------+------+-----+---------+----------------------------------+






相关推荐
在Snort的早期版本中,它包含了用于存储日志数据的数据库结构,这使得用户能够将Snort捕获的事件导入到数据库以便于分析和长期存储。然而,从2.9版本开始,Snort默认不再包含`schemas`模块,这导致用户在尝试将日志...
Snort 数据库结构分析 Snort 是一个开源的入侵检测系统,能够实时监控网络流量,检测和防止网络攻击。Snort 数据库结构是 Snort 系统的核心组件,用于存储和管理检测到的告警事件和相关信息。本文将详细介绍 Snort ...
2. **安装Snort并选择支持的数据库类型**:在安装Snort时,选择支持的数据库类型(这里以SQL Server为例)。 3. **创建数据库用户**:在SQL Server中创建一个专门用于管理Snort数据库的用户,例如“snortuser”,并...
在安装 Snort 的过程中,我们需要注意一些重要的细节,例如选择正确的安装路径、配置 MySQL 数据库服务器、创建 Snort 数据库等。只有通过正确的安装和配置,我们才能确保 Snort 正常运行,检测和防御网络攻击。 在...
Barnyard2 是 Snort 的一个数据库输出插件,可以将Snort 的日志信息存储到数据库中。以下是 Barnyard2 的安装和配置步骤: 1. 下载 Barnyard2 的安装包。 2. 安装 Barnyard2,包括编译和安装 Barnyard2 的核心组件...
Snort是一款开源的网络入侵检测系统(NIDS),它能够实时监控网络流量,识别并防止潜在的攻击。本文将深入探讨Snort规则及其在版本2900中的应用。 Snort规则是Snort系统的核心,它们定义了Snort如何识别和响应网络...
MySQL 是一个开源的关系型数据库管理系统,用于存储 Snort 产生的日志数据。Snort 在检测到网络活动时会生成事件,这些事件被 MySQL 存储并组织起来,方便查询和分析。 3. PHP 脚本语言: PHP 作为服务器端脚本语言...
创建一个Snort使用的数据库和用户,执行初始化脚本以创建所需的表结构。在snort.conf中配置数据库连接信息,包括用户名、密码、主机名和数据库名。 7)安装adodb组件: ADODB是一个PHP数据库抽象层,用于连接Snort...
mysql -u root -p snort 初始化数据库 cd /usr/local/snort/ mkdir -p /usr/local/snort/etc //建立配置文件夹 mkdir -p /usr/local/snort/rules //建立规则文件夹 cp /usr/src/rules/* /usr/local/snort/rules...
第二章《系统初始化》详细阐述了Snort启动时的配置解析和环境准备过程。Snort读取配置文件,解析规则、设置检测策略,并初始化各种插件。这一章节对于理解Snort如何根据用户需求定制其行为至关重要。 第三章《打开...
5. `acid-0.9.6b23.tar.gz`:ACID(Analyzer for Correlated Intrusion Data)是基于PHP的Snort事件分析和报告数据库,可以与BASE一起使用,以提供更强大的日志管理和分析功能。 6. `Snort2.8.6`和`Snort2.9.16`:...
综上所述,《Snort源码分析》全面覆盖了Snort从系统初始化到数据包处理的整个生命周期,深入解析了其核心组件和机制,是理解Snort工作原理的宝贵资源。通过学习这本书,读者可以掌握如何利用Snort进行网络监控,增强...
### Snort源码分析:规则初始化引擎深度剖析 在网络安全领域,Snort作为一个开源的入侵检测系统(IDS),以其高效性和灵活性著称。其核心功能在于通过对网络数据包的实时监控,比对预设的入侵特征规则,及时发现并...
- 安装Web界面通常涉及部署Web服务器(如Apache或Nginx)、数据库(如MySQL)以及Web应用。 - 配置Web应用连接到Snort,读取日志并展示可视化报告,便于监控和响应安全事件。 6. **优化与维护**: - 定期更新...
在数据库标签的上下文中,Snort可能与数据库相关的攻击检测有关,例如监控SQL注入尝试或未经授权的数据库访问。Snort的规则可以配置来识别这些活动,保护数据库服务器免受攻击。 总的来说,Snort是一个强大的工具,...
Snort是一种开源网络入侵检测系统(NIDS),它通过分析网络流量来识别潜在的攻击行为。Snort规则是Snort系统的核心,它们定义了Snort应如何响应特定的网络活动。在版本2853中,这些规则经过更新和优化,以适应不断...
为了存储警报信息,Snort可以与MySQL数据库集成。首先,创建数据库结构: ```bash mysql -u root -p ``` 接着,确保PHP环境支持MySQL,以便后续的Web界面访问: ```bash yum install httpd ...