一.测试拓扑:
备注:因为51cto会屏蔽VPN关键字,所以把51cto原创的一些博文移到这边。

二.测试目的:
A.理解DMVPN的阶段二和阶段三
B.验证两种方式穿越PAT的不同
三.基本配置:
A.Hub:
interface Loopback0
ip address 192.168.100.1 255.255.255.0
interface FastEthernet0/0
ip address 202.100.1.100 255.255.255.0
no shut
B.Branch1:
interface FastEthernet0/0
ip address 202.100.1.1 255.255.255.0
interface FastEthernet0/1
ip address 10.1.1.10 255.255.255.0
no shut
C.Branch2:
interface FastEthernet0/0
ip address 202.100.1.2 255.255.255.0
no shut
interface FastEthernet0/1
ip address 10.1.1.10 255.255.255.0
no shut
D:Spoke1:
interface Loopback0
ip address 192.168.1.1 255.255.255.0
interface FastEthernet0/0
ip address 10.1.1.1 255.255.255.0
no shut
ip route 0.0.0.0 0.0.0.0 10.1.1.10
E:Spoke2:
interface Loopback0
ip address 192.168.2.1 255.255.255.0
interface FastEthernet0/0
ip address 10.1.1.1 255.255.255.0
no shut
ip route 0.0.0.0 0.0.0.0 10.1.1.10
三.动态PAT配置:
A.PAT配置:
ip access-list extended pat
permit ip any any
int f0/0
ip nat outside
int f0/1
ip nat inside
ip nat inside source list pat interface f0/0 overload
B.测试:
Spoke1#ping 202.100.1.100
Type escape sequence to abort.
Sending 5, 100-byte ICMP Echos to 202.100.1.100, timeout is 2 seconds:
!!!!!
Success rate is 100 percent (5/5), round-trip min/avg/max = 52/89/152 ms
Spoke2#ping 202.100.1.100
Type escape sequence to abort.
Sending 5, 100-byte ICMP Echos to 202.100.1.100, timeout is 2 seconds:
!!!!!
Success rate is 100 percent (5/5), round-trip min/avg/max = 64/119/280 ms
四.DMVPN阶段二配置:
A.mGRE和NHRP配置:
①.Hub:
interface Tunnel0
ip address 172.16.1.100 255.255.255.0
tunnel source FastEthernet0/0
tunnel mode gre multipoint
tunnel key 12345
ip nhrp network-id 10
ip nhrp authentication cisco
ip nhrp map multicast dynamic
②.Spoke1:
interface Tunnel0
ip address 172.16.1.1 255.255.255.0
tunnel source FastEthernet0/0
tunnel mode gre multipoint
tunnel key 12345
ip nhrp network-id 10
ip nhrp authentication cisco
ip nhrp map 172.16.1.100 202.100.1.100
ip nhrp map multicast 202.100.1.100
ip nhrp nhs 172.16.1.100
③.Spoke2:
interface Tunnel0
ip address 172.16.1.2 255.255.255.0
tunnel source FastEthernet0/0
tunnel mode gre multipoint
tunnel key 12345
ip nhrp network-id 10
ip nhrp authentication cisco
ip nhrp map 172.16.1.100 202.100.1.100
ip nhrp map multicast 202.100.1.100
ip nhrp nhs 172.16.1.100
B.验证NHRP注册:
①Hub#show ip nhrp
172.16.1.1/32 via 172.16.1.1, Tunnel0 created 00:03:34, expire 01:56:25
Type: dynamic, Flags: unique registered
NBMA address: 202.100.1.1
(Claimed NBMA address: 10.1.1.1)
172.16.1.2/32 via 172.16.1.2, Tunnel0 created 00:00:46, expire 01:59:13
Type: dynamic, Flags: unique registered
NBMA address: 202.100.1.2
(Claimed NBMA address: 10.1.1.1)
②Spoke1#show ip nhrp
172.16.1.100/32 via 172.16.1.100, Tunnel0 created 00:04:16, never expire
Type: static, Flags: used
NBMA address: 202.100.1.100
③Spoke2#show ip nhrp
172.16.1.100/32 via 172.16.1.100, Tunnel0 created 00:02:11, never expire
Type: static, Flags: used
NBMA address: 202.100.1.100
C.验证mGRE:
①Spoke1#ping 172.16.1.100 source 172.16.1.1
Type escape sequence to abort.
Sending 5, 100-byte ICMP Echos to 172.16.1.100, timeout is 2 seconds:
Packet sent with a source address of 172.16.1.1
!!!!!
②Spoke2#ping 172.16.1.100 source 172.16.1.2
Type escape sequence to abort.
Sending 5, 100-byte ICMP Echos to 172.16.1.100, timeout is 2 seconds:
Packet sent with a source address of 172.16.1.2
!!!!!
③Spoke1#ping 172.16.1.2 source 172.16.1.1
Type escape sequence to abort.
Sending 5, 100-byte ICMP Echos to 172.16.1.2, timeout is 2 seconds:
Packet sent with a source address of 172.16.1.1
!!!!!
Spoke1#show ip nhrp
172.16.1.1/32 via 172.16.1.1, Tunnel0 created 00:00:04, expire 01:59:55
Type: dynamic, Flags: router unique local
NBMA address: 10.1.1.1
(no-socket)
172.16.1.2/32 via 172.16.1.2, Tunnel0 created 00:00:05, expire 01:59:56
Type: dynamic, Flags: router
NBMA address: 202.100.1.2
(Claimed NBMA address: 10.1.1.1)
172.16.1.100/32 via 172.16.1.100, Tunnel0 created 00:07:54, never expire
Type: static, Flags: used
NBMA address: 202.100.1.100
Spoke2#show ip nhrp
172.16.1.1/32 via 172.16.1.1, Tunnel0 created 00:01:04, expire 01:58:54
Type: dynamic, Flags: router
NBMA address: 202.100.1.1
(Claimed NBMA address: 10.1.1.1)
172.16.1.2/32 via 172.16.1.2, Tunnel0 created 00:01:04, expire 01:58:57
Type: dynamic, Flags: router unique local
NBMA address: 10.1.1.1
(no-socket)
172.16.1.100/32 via 172.16.1.100, Tunnel0 created 00:06:25, never expire
Type: static, Flags: used
NBMA address: 202.100.1.10
D.动态路由配置及优化:
①Hub:
router eigrp 100
network 172.16.1.0 0.0.0.255
network 192.168.100.0
no auto-summary
int tun 0
no ip next-hop-self eigrp 100
no ip split-horizon eigrp 100
②Spoke1:
router eigrp 100
network 172.16.1.0 0.0.0.255
network 192.168.1.0
no auto-summary
③Spoke2:
router eigrp 100
network 172.16.1.0 0.0.0.255
network 192.168.2.0
no auto-summary
④验证:
Hub#show ip route eigrp
D 192.168.1.0/24 [90/297372416] via 172.16.1.1, 00:01:39, Tunnel0
D 192.168.2.0/24 [90/297372416] via 172.16.1.2, 00:00:10, Tunnel0
Spoke1#show ip route eigrp
D 192.168.2.0/24 [90/310172416] via 172.16.1.2, 00:00:52, Tunnel0
D 192.168.100.0/24 [90/297372416] via 172.16.1.100, 00:02:27, Tunnel0
Spoke2#show ip route eigrp
D 192.168.1.0/24 [90/310172416] via 172.16.1.1, 00:01:25, Tunnel0
D 192.168.100.0/24 [90/297372416] via 172.16.1.100, 00:01:25, Tunnel0
E.IPSEC 配置:
①配置:
crypto isakmp policy 10
authentication pre-share
crypto isakmp key cisco address 0.0.0.0 0.0.0.0
crypto ipsec transform-set transet esp-des esp-md5-hmac
mode transport
crypto ipsec profile ipsecprofile
set transform-set transet
int tun 0
ip mtu 1400
tunnel protection ipsec profile ipsecprofile
②验证:
Hub#show crypto engine conn active
Crypto Engine Connections
ID Interface Type Algorithm Encrypt Decrypt IP-Address
1 Fa0/0 IPsec DES+MD5 0 17 202.100.1.100
2 Fa0/0 IPsec DES+MD5 20 0 202.100.1.100
3 Fa0/0 IPsec DES+MD5 0 17 202.100.1.100
4 Fa0/0 IPsec DES+MD5 18 0 202.100.1.100
1001 Fa0/0 IKE SHA+DES 0 0 202.100.1.100
1002 Fa0/0 IKE SHA+DES 0 0 202.100.1.100
Spoke1#show crypto engine connections active
Crypto Engine Connections
ID Interface Type Algorithm Encrypt Decrypt IP-Address
1 Tu0 IPsec DES+MD5 0 25 10.1.1.1
2 Tu0 IPsec DES+MD5 22 0 10.1.1.1
1001 Tu0 IKE SHA+DES 0 0 10.1.1.1
Spoke2#show crypto engine conn active
Crypto Engine Connections
ID Interface Type Algorithm Encrypt Decrypt IP-Address
1 Tu0 IPsec DES+MD5 0 29 10.1.1.1
2 Tu0 IPsec DES+MD5 28 0 10.1.1.1
1001 Tu0 IKE SHA+DES 0 0 10.1.1.1
-----------spoke之间没有加密流量----------------------------------
Spoke1#ping 192.168.2.1 source 192.168.1.1 repeat 100
Type escape sequence to abort.
Sending 100, 100-byte ICMP Echos to 192.168.2.1, timeout is 2 seconds:
Packet sent with a source address of 192.168.1.1
!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!
!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!
Success rate is 100 percent (100/100), round-trip min/avg/max = 188/253/520 ms
Spoke1#show crypto engine connections active
Crypto Engine Connections
ID Interface Type Algorithm Encrypt Decrypt IP-Address
1 Tu0 IPsec DES+MD5 0 154 10.1.1.1
2 Tu0 IPsec DES+MD5 150 0 10.1.1.1
1001 Tu0 IKE SHA+DES 0 0 10.1.1.1
-----------spoke之间仍然没有加密流量,都走的是hub做中转-----------------
四.DMVPN阶段三配置:
主要配置与阶段二相同,主要不同点:
①NHRP优化:
HUB:
int tun 0
ip nhrp redirect
Spoke:
int tun 0
ip nhrp shortcut
②hub发布汇总路由,取消印制水平分割和下一跳:
HUB:
int tun 0
ip summary-address eigrp 100 192.168.0.0 255.255.0.0
ip split-horizon eigrp 100
ip next-hop-self eigrp 100
③验证路由汇总:
Spoke1#show ip route eigrp
D 192.168.0.0/16 [90/297372416] via 172.16.1.100, 00:00:47, Tunnel0
Spoke2#show ip route eigrp
D 192.168.0.0/16 [90/297372416] via 172.16.1.100, 00:01:08, Tunnel0
④isakmp sa验证:
Hub#show crypto isakmp sa
IPv4 Crypto ISAKMP SA
dst src state conn-id slot status
202.100.1.100 202.100.1.1 QM_IDLE 1007 0 ACTIVE
202.100.1.100 202.100.1.2 QM_IDLE 1008 0 ACTIVE
Spoke1#show crypto is
Spoke1#show crypto isakmp sa
IPv4 Crypto ISAKMP SA
dst src state conn-id slot status
202.100.1.100 10.1.1.1 QM_IDLE 1004 0 ACTIVE
Spoke2#show crypto isakmp sa
IPv4 Crypto ISAKMP SA
dst src state conn-id slot status
202.100.1.100 10.1.1.1 QM_IDLE 1004 0 ACTIVE
------------spoke之间没有建立isakmp sa--------------------------
Spoke1#ping 192.168.2.1 source 192.168.1.1 repeat 100
Type escape sequence to abort.
Sending 100, 100-byte ICMP Echos to 192.168.2.1, timeout is 2 seconds:
Packet sent with a source address of 192.168.1.1
!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!
!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!
Success rate is 100 percent (100/100), round-trip min/avg/max = 180/252/552 ms
Spoke1#show crypto isakmp sa
IPv4 Crypto ISAKMP SA
dst src state conn-id slot status
202.100.1.2 10.1.1.1 MM_NO_STATE 0 0 ACTIVE (deleted)
202.100.1.100 10.1.1.1 QM_IDLE 1004 0 ACTIVE
Spoke2#show crypto isakmp sa
IPv4 Crypto ISAKMP SA
dst src state conn-id slot status
202.100.1.100 10.1.1.1 QM_IDLE 1004 0 ACTIVE
202.100.1.1 10.1.1.1 MM_NO_STATE 0 0 ACTIVE
------------spoke之间main mode没有协商成功-----------------------
④Branch1更改动态PAT为静态PAT:
Branch1:
ip nat inside source list pat interface FastEthernet0/0 overload
ip nat inside source static udp 10.1.1.1 500 interface FastEthernet0/0 500
ip nat inside source static udp 10.1.1.1 4500 interface FastEthernet0/0 4500
关闭所有tunnel接口,并重新开启,由spoke1作为发起方:
发起之前:
Spoke1#show crypto isakmp sa
IPv4 Crypto ISAKMP SA
dst src state conn-id slot status
202.100.1.100 10.1.1.1 QM_IDLE 0 0 ACTIVE
发起流量:
Spoke1#ping 192.168.2.1 source 192.168.1.1
Type escape sequence to abort.
Sending 5, 100-byte ICMP Echos to 192.168.2.1, timeout is 2 seconds:
Packet sent with a source address of 192.168.1.1
!!!!!
Spoke1#show crypto isakmp sa
IPv4 Crypto ISAKMP SA
dst src state conn-id slot status
202.100.1.2 10.1.1.1 MM_NO_STATE 0 0 ACTIVE
202.100.1.100 10.1.1.1 QM_IDLE 1009 0 ACTIVE
10.1.1.1 202.100.1.2 QM_IDLE 1010 0 ACTIV
Spoke1#show crypto engine conn active
Crypto Engine Connections
ID Interface Type Algorithm Encrypt Decrypt IP-Address
15 Tu0 IPsec DES+MD5 0 43 10.1.1.1
16 Tu0 IPsec DES+MD5 42 0 10.1.1.1
17 Fa0/0 IPsec DES+MD5 0 2 10.1.1.1
18 Fa0/0 IPsec DES+MD5 1 0 10.1.1.1
1009 Tu0 IKE SHA+DES 0 0 10.1.1.1
1010 Fa0/0 IKE SHA+DES 0 0 10.1.1.1
Spoke1#ping 192.168.2.1 source 192.168.1.1 repeat 100
Type escape sequence to abort.
Sending 100, 100-byte ICMP Echos to 192.168.2.1, timeout is 2 seconds:
Packet sent with a source address of 192.168.1.1
!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!
!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!
Success rate is 100 percent (100/100), round-trip min/avg/max = 140/191/260 ms
Spoke1#show crypto engine conn active
Crypto Engine Connections
ID Interface Type Algorithm Encrypt Decrypt IP-Address
15 Tu0 IPsec DES+MD5 0 54 10.1.1.1
16 Tu0 IPsec DES+MD5 53 0 10.1.1.1
17 Fa0/0 IPsec DES+MD5 0 102 10.1.1.1
18 Fa0/0 IPsec DES+MD5 101 0 10.1.1.1
1009 Tu0 IKE SHA+DES 0 0 10.1.1.1
1010 Fa0/0 IKE SHA+DES 0 0 10.1.1.1
Spoke2#show crypto ipsec sa
interface: Tunnel0
Crypto map tag: Tunnel0-head-0, local addr 10.1.1.1
protected vrf: (none)
local ident (addr/mask/prot/port): (10.1.1.1/255.255.255.255/47/0)
remote ident (addr/mask/prot/port): (202.100.1.1/255.255.255.255/47/0)
current_peer 202.100.1.1 port 4500
PERMIT, flags={origin_is_acl,}
#pkts encaps: 102, #pkts encrypt: 102, #pkts digest: 102
#pkts decaps: 101, #pkts decrypt: 101, #pkts verify: 101
---------前面的几个包有中心代转,后面是spoke之间直接通讯-----------
关闭所有tunnel接口,并重新开启,由spoke2作为发起方:
发起之前:
Spoke2#show crypto isakmp sa
IPv4 Crypto ISAKMP SA
dst src state conn-id slot status
202.100.1.100 10.1.1.1 QM_IDLE 1010 0 ACTIVE
发起流量:
Spoke2#ping 192.168.1.1 sou
Spoke2#ping 192.168.1.1 source 192.168.2.1
Type escape sequence to abort.
Sending 5, 100-byte ICMP Echos to 192.168.1.1, timeout is 2 seconds:
Packet sent with a source address of 192.168.2.1
!!!!!
Success rate is 100 percent (5/5), round-trip min/avg/max = 204/368/464 ms
Spoke2#show crypto isakmp sa
IPv4 Crypto ISAKMP SA
dst src state conn-id slot status
202.100.1.100 10.1.1.1 QM_IDLE 1010 0 ACTIVE
202.100.1.1 10.1.1.1 QM_IDLE 1011 0 ACTIVE
Spoke2#show crypto engine conn act
Crypto Engine Connections
ID Interface Type Algorithm Encrypt Decrypt IP-Address
19 Tu0 IPsec DES+MD5 0 56 10.1.1.1
20 Tu0 IPsec DES+MD5 58 0 10.1.1.1
21 Tu0 IPsec DES+MD5 0 1 10.1.1.1
22 Tu0 IPsec DES+MD5 1 0 10.1.1.1
1010 Tu0 IKE SHA+DES 0 0 10.1.1.1
1011 Tu0 IKE SHA+DES 0 0 10.1.1.1
Spoke2#show crypto engine conn act
Crypto Engine Connections
ID Interface Type Algorithm Encrypt Decrypt IP-Address
19 Tu0 IPsec DES+MD5 0 65 10.1.1.1
20 Tu0 IPsec DES+MD5 67 0 10.1.1.1
21 Tu0 IPsec DES+MD5 0 101 10.1.1.1
22 Tu0 IPsec DES+MD5 101 0 10.1.1.1
1010 Tu0 IKE SHA+DES 0 0 10.1.1.1
1011 Tu0 IKE SHA+DES 0 0 10.1.1.1
Spoke2#show crypto ipsec sa
interface: Tunnel0
Crypto map tag: Tunnel0-head-0, local addr 10.1.1.1
protected vrf: (none)
local ident (addr/mask/prot/port): (10.1.1.1/255.255.255.255/47/0)
remote ident (addr/mask/prot/port): (202.100.1.1/255.255.255.255/47/0)
current_peer 202.100.1.1 port 4500
PERMIT, flags={origin_is_acl,}
#pkts encaps: 101, #pkts encrypt: 101, #pkts digest: 101
#pkts decaps: 101, #pkts decrypt: 101, #pkts verify: 101
---------前面的几个包有中心代转,后面是spoke之间直接通讯-----------
⑤保留静态PAT,恢复成阶段二进行测试:
Spoke1#show crypto isakmp sa
IPv4 Crypto ISAKMP SA
dst src state conn-id slot status
202.100.1.100 10.1.1.1 QM_IDLE 1013 0 ACTIVE
Spoke1#ping 192.168.2.1 source 192.168.1.1
Type escape sequence to abort.
Sending 5, 100-byte ICMP Echos to 192.168.2.1, timeout is 2 seconds:
Packet sent with a source address of 192.168.1.1
!!!.!
Success rate is 80 percent (4/5), round-trip min/avg/max = 180/421/624 ms
抓包看到有spoke2首先发起IPSEC连接:
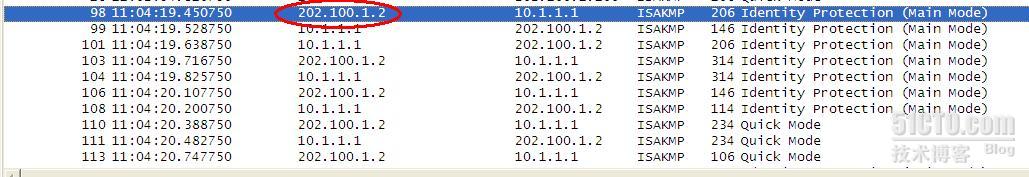
Spoke1#show crypto isakmp sa
IPv4 Crypto ISAKMP SA
dst src state conn-id slot status
202.100.1.2 10.1.1.1 MM_NO_STATE 0 0 ACTIVE
202.100.1.100 10.1.1.1 QM_IDLE 1013 0 ACTIVE
10.1.1.1 202.100.1.2 QM_IDLE 1014 0 ACTIVE
Spoke1#show crypto engine conn act
Crypto Engine Connections
ID Interface Type Algorithm Encrypt Decrypt IP-Address
23 Tu0 IPsec DES+MD5 0 48 10.1.1.1
24 Tu0 IPsec DES+MD5 45 0 10.1.1.1
25 Fa0/0 IPsec DES+MD5 0 3 10.1.1.1
26 Fa0/0 IPsec DES+MD5 2 0 10.1.1.1
1013 Tu0 IKE SHA+DES 0 0 10.1.1.1
1014 Fa0/0 IKE SHA+DES 0 0 10.1.1.1
Spoke1#ping 192.168.2.1 source 192.168.1.1 repeat 100
Type escape sequence to abort.
Sending 100, 100-byte ICMP Echos to 192.168.2.1, timeout is 2 seconds:
Packet sent with a source address of 192.168.1.1
!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!
!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!
Success rate is 100 percent (100/100), round-trip min/avg/max = 144/194/276 ms
Spoke1#ping 192.168.2.1 source 192.168.1.1 repeat 100
Spoke1#show crypto engine conn act
Crypto Engine Connections
ID Interface Type Algorithm Encrypt Decrypt IP-Address
23 Tu0 IPsec DES+MD5 0 62 10.1.1.1
24 Tu0 IPsec DES+MD5 59 0 10.1.1.1
25 Fa0/0 IPsec DES+MD5 0 103 10.1.1.1
26 Fa0/0 IPsec DES+MD5 102 0 10.1.1.1
1013 Tu0 IKE SHA+DES 0 0 10.1.1.1
1014 Fa0/0 IKE SHA+DES 0 0 10.1.1.1
Spoke1#show crypto ipsec sa
interface: Tunnel0
Crypto map tag: Tunnel0-head-0, local addr 10.1.1.1
protected vrf: (none)
local ident (addr/mask/prot/port): (10.1.1.1/255.255.255.255/47/0)
remote ident (addr/mask/prot/port): (202.100.1.2/255.255.255.255/47/0)
current_peer 202.100.1.2 port 4500
PERMIT, flags={origin_is_acl,}
#pkts encaps: 102, #pkts encrypt: 102, #pkts digest: 102
#pkts decaps: 103, #pkts decrypt: 103, #pkts verify: 103
五.总结:
A.当spoke都位于动态PAT设备后面,spoke之间的通讯流量都由中心代转
B.当某个spoke位于静态PAT设备后面,它能跟其他动态PAT后面的spoke直接通讯,而不管发起发是哪个
C.以上对DMVPN第二阶段和第三阶段都适用
D.测试的IOS为:
Cisco IOS Software, 3700 Software (C3725-ADVENTERPRISEK9-M), Version 12.4(15)T14, RELEASE SOFTWARE (fc2)






相关推荐
- **DMVPN技术**:动态多点虚拟专用网(Dynamic Multipoint Virtual Private Network, DMVPN)提供了一种灵活的网络互联方式,尤其是在构建分布式网络时非常有用。 #### 四、IOU仿真验证 为了验证上述优化方案的...
AToM 和 VPLS ), QoS ,核心网络 MPLS 流量工程( TE )和可管理的安全服务(如 Firewall/NAT 托管, EZVPN , DMVPN 等)。同时为进一步优化运营商 IP及其相关服务的管理流程, ISC 还率先实现了对 IP服务开通的...
AToM 和 VPLS ), QoS ,核心网络 MPLS 流量工程( TE )和可管理的安全服务(如 Firewall/NAT 托管, EZVPN , DMVPN 等)。同时为进一步优化运营商 IP 及其相关服务的管理流程, ISC 还率先实现了对 IP服务开通的...
AToM 和 VPLS ), QoS ,核心网络 MPLS 流量工程( TE )和可管理的安全服务(如 Firewall/NAT 托管, EZVPN , DMVPN 等)。同时为进一步优化运营商 IP 及其相关服务的管理流程, ISC 还率先实现了对 IP 服务开通...
AToM 和 VPLS ), QoS ,核心网络 MPLS 流量工程( TE )和可管理的安全服务(如 Firewall/NAT 托管, EZVPN , DMVPN 等)。同时为进一步优化运营商 IP VPN 及其相关服务的管理流程, ISC 还率先实现了对 IP VPN ...
DMVPN手册 DMVPN(BGP)手册 IPSEC和BGP手册 IPSEC和GRE手册 局域网剧本 用户创建和SSH密钥手册 阅读要求以拥有成功的运行时。 要求 点3 Python3 Openssh服务器 SSH密钥 帕拉米科 Ansible 虚拟操作系统 ...
OpenNHRP实现NBMA下一跳解析协议(在RFC 2332中定义)。 它使使用NHRP,GRE和IPsec创建动态多点VPN Linux路由器成为可能。 它旨在与Cisco DMVPN兼容。
在配置和管理汽车网络时,需要注意网络的安全性和稳定性,例如在配置DMVPN时,必须确保ISAKMP(Internet Security Association and Key Management Protocol)的预共享密钥配置正确,避免出现错误的认证设置,影响...
3. **WAN优化**:通过动态隧道、DMVPN(Dial-on-Demand Routing over Multiprotocol Label Switching Virtual Private Network,按需拨号多协议标签交换虚拟私有网络)等技术提升网络性能。 4. **集中策略管理与报告...
此外,还有针对VoIP的sRTP、DMVPN、MPLS & IPSec等技术,为网络提供安全的扩展连接。 7. **协作式安全**:思科的NAC架构解决方案与Intel的AMT(主动管理技术)相结合,实现了对网络设备的配置状态审计和修复,确保...
思科的iWAN架构还包括了多个安全层面的技术,例如DMVPN和IPsec的覆盖设计、Performance Routing(PfR)、ASA和IOS Firewall/IPS的综合威胁防护以及云端网络安全(CWS)服务。这些安全措施确保了网络连接的安全性,并且...
- 动态多点VPN(DMVPN)、最佳努力带宽(Best Effort)等技术的应用也得到了详细介绍。 - **无线LAN基础设施**: - 基于WLAN的语音和视频通信架构,强调了无线网络在现代办公环境中不可或缺的作用。 ##### 四、网络...
对于那些不使用自适应QoS用于DMVPN功能的客户,可以通过设置COPP策略来拒绝所有到达受影响设备上的UDP端口18999的流量。例如,可以创建如下配置: ```conf !-- ACL for CoPP Undesirable UDP class-map access-list...
分析目前校园网络存在的问题,以某高校的校园网建设为研究对象,通过整合校园网络资源,提出一种基于私有云计算的信息交互模型,该模型包含用户层、服务层和资源层,采用该模型可以满足用户随时随地通过...